March 23, 2017
The Latest on the Reported iPhone Hack
 There are currently some high-profile stories in the news about alleged foreign hackers who claim to have the ability to wipe out the contents of millions of iPhones and iPad worldwide.
There are currently some high-profile stories in the news about alleged foreign hackers who claim to have the ability to wipe out the contents of millions of iPhones and iPad worldwide.March 23, 2017
 There are currently some high-profile stories in the news about alleged foreign hackers who claim to have the ability to wipe out the contents of millions of iPhones and iPad worldwide.
There are currently some high-profile stories in the news about alleged foreign hackers who claim to have the ability to wipe out the contents of millions of iPhones and iPad worldwide.March 15, 2017
 If you’re still using Microsoft
If you’re still using Microsoft Entourage, then you’re playing with fire. Entourage is the email program that was included as part of Microsoft’s 2008 Office suite. At one point, it was the best mail client for Mac, bar none. But because it was introduced in early 2008, it means you’re using software that was cutting edge nine years ago. So do you really want to trust an important part of your world – email – with an outdated product? It’s starting to show its age and give users all sorts of problems. Microsoft no longer supports Entourage. And because it’s been obsolete for almost seven years, it’s time to look elsewhere for your email program.
There are a few options to replace Entourage, but they all have their plusses and minuses.
Microsoft Outlook: This is the successor to Entourage. Yes, the Mac-compatible version of Microsoft’s mail program was called Outlook back in the dark ages, but the big brains there gave the Mac product a separate name to differentiate it from the Windows mail program.
There have been two versions of Outlook released since the Entourage days: Office 2011 and Office 365. Office 2011 (still available and not problematic – yet) is a standard “buy it” software package, while the Office 365 suite is a yearly subscription model. Both include updated versions of Word, Excel, PowerPoint and some other stuff nobody uses. There are a few different options for both.
BUT – a couple of important things to note. One, there are different versions of the Office 2011 suite, and some of them DO NOT include Outlook. So shop carefully. Also, if you use Entourage and want to retain all your old email when you upgrade to Office 365’s version of Outlook, you can’t do a direct import into Outlook. You have upgrade your mail to Outlook 2011 first, and THEN import it to Outlook 365. (Ugh.) But that’s what you call me for!
Web-based mail: More and more people are using Web-based mail. Sounds complex, but it isn’t. For example, if you’re a Gmail user, you open your browser of choice and use your email that way. That’s not quite as user-friendly as using a stand-alone mail program (Outlook, Apple Mail, etc.), but workable. Most of these also allow you to store your contacts as well. Another downside of this method is that it’s tough to do this on your iPhone.
But – if you’re using Gmail, there IS a Gmail program for Mac available in the App Store. (It’s called “Viewer For Gmail.”) That’s a good way to get a little more user-friendliness from your email client.
Of course, the best bet (though that wasn’t always the case) is Apple’s mail client, cleverly called “Mail.” It’s in your APPLICATIONS folder and it’s designed to not only manage your mail, but to interact seamlessly with Contacts (Apple’s built-in address book), Calendar (Apple’s calendar) and your iPhone and iPad, using iCloud.
![]() Apple mail used to have a reputation of being cranky, mostly when it came to the outgoing servers. And it still has issues with rinky-dink mail providers. But as long as you’re using the big boys for your email (Google, 1and1, etc.), you’ll be fine.
Apple mail used to have a reputation of being cranky, mostly when it came to the outgoing servers. And it still has issues with rinky-dink mail providers. But as long as you’re using the big boys for your email (Google, 1and1, etc.), you’ll be fine.
February 8, 2017
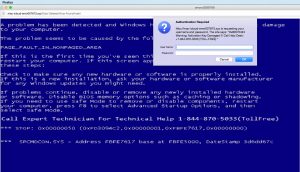
This scam just hit a client’s computer earlier this week. Don’t let a stranger tell you that there’s something wrong with your computer!
It’s something that has happened to everybody; you’re working, minding your own business, surfing the web, and suddenly your reverie is broken. A window alerts you that there’s a problem with your computer; your data is going to be corrupted; all your browsing history will be displayed for everybody to see; or simply there’s a virus and it need to be fixed NOW! And just for your utter convenience, there’s a number to call for these honest and helpful folks to solve the issue. All major credit cards accepted.
Sometimes it’s just a pop-up window; other times it hijacks your entire screen and there’s seemingly no escape. Either way, it’s a scam and should be aggressively ignored. Remember – no stranger should give you unsolicited advice that your computer has a problem that only they can fix.
Think about it; somebody you don’t know and has no access to your computer should NOT know anything about your computer (other than a few inconsequential technical details.) So, assuming they can detect a virus or other problem is wrong; those are scams that should be ignored.
If you DO call their number, you can easily tell you’re speaking to a call center located on the other side of the planet. The noise in the background is one dead giveaway; the accents of the agents is another. Most of these scammers are trying to sell you a solution to your “problem,” which just involves paying for a service you don’t need. But others are more devious; scouring your computer for sensitive information, including passwords to online accounts, Social Security numbers or financial data.
Bottom line; don’t fall for the scam. At the first sign of ANY funny business, quit your browser and clear your browsing history. If the problem persists, switch to another browser. (Some of these scams involve the scrubbing of the preference files of your browser to get things back to normal.) If necessary, employ the services of a trusted computer professional. NEVER call these companies (much less let them gain access to your computer); once they get your phone number in their database, the harassment will never end. And since they’re largely overseas, they laugh at the mention of the National Do Not Call Registry or any threats of lawsuits.
January 17, 2017
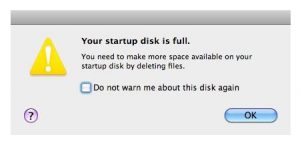
A message that requires action ASAP!
Funny thing, but digging through the archives, I found that I covered this very subject in the first blog post of 2016! But seeing that I’ve gotten three calls about the dreaded full hard drive warning in the past two weeks, I figure it’s a good time to revisit it. Besides maintaining a backup of your data as well as practicing good hard drive hygiene is one of the most important things I stress.
The implications of having a full hard drive are serious: There is a risk of crashing (and losing valuable data), which should be enough of a deterrent. Also, there’s sluggishness which is often accompanied by decreased functionality. Ignoring the problem by disabling the warning isn’t an option either. The problem of a nearly full drive can be easily solved by knowing exactly what data you can live without on your computer (or at least offload to an external device).
So what exactly takes up the most space?
Music, movies, photos and large graphic art files are the biggest culprits. Photo and music libraries of 100GB (or more) are extremely common. But unless these things are offloaded onto an external drive, they are what they are. Having them reside on an external drive isn’t a bad idea in theory, but a couple of things need be heeded.
For one, you must understand that the external drive must be connected if you want to access the files on it. Not a problem (for the most part) if you’re using a desktop Mac; if you’re a laptop user, then there’s that pesky little step of connecting the drive (and toting with you if you need to access them elsewhere). Not that convenient. Plus, you need to remember to back it up to your normal backup process. Which would mean connecting it to a computer. Life would stink if you lost your only copy of your music or (especially) your pictures.
But there ARE some ways to reduce the number of gigabytes clogging up your hard drive. These include deleting:
But – run your back up process BEFORE trashing any files!
December 1, 2016
Same warranty as a new Apple product!
One thing that Apple is never shy about; preventing prices from getting too low for its products. Today’s prices are never going to go down – you’re simply going to get a better computer for the same money. And forget about shopping around – Apple controls its pricing through its authorized dealers across the board with a heavy hand.
That’s not to say there aren’t ways to save a few bucks. And I’m not talking about buying used at estate sales, local tag sale groups (on Facebook, for example), eBay or craigslist. (I check the prices on these places, and there rarely seems to be any bargains there.) Besides, when buying from a stranger (either in person or online), you don’t know the history, problems, etc. with the computer or device you’re buying. There is no Carfax for electronic devices; unless you get some sort of money-back guarantee from the seller, you’ll probably be out of luck if things go sour and you want to make the deal null and void.
But don’t despair! There are a couple of options – one is through Apple itself, and its refurb store. The other involves third-party dealers – but it requires that you subscribe to sales emails from these companies. (Or check their sales pages when you’re looking to buy.)
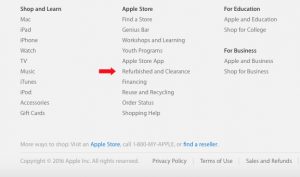
Where the refurb link is lurking – at the bottom of Apple.com.
First of all – Apple’s “Refurbished” store. It’s a bit tough to find – the link is at the bottom of its homepage, almost an afterthought. Click on it and you’ll see a sampling of what’s available. The good news is that these computers and devices have the same Apple warranty as a new model. You can generally save $100 or more on this page; you can go to Apple’s homepage and look for it, or go straight to it here. But there are a couple of things you need to know.
For one, these deals are ONLY available online, so walking into the Apple Store isn’t going to help. And because of the mail-only limitations, it’s not going to work for a “need it today” type of situation. A little advance planning is required if you’re going this route. Check out this great article – The Top Six Places To Buy Refurbished Mac Laptops.
A second option is to subscribe to emails from some of the larger Apple dealers. These retailers often can discount recently discontinued models – giving around the same break as Apple and its refurbs. Of course, you must deal with a regular stream of email messages during the times you don’t plan on buying anything. Regardless, a couple of these are:
November 7, 2016
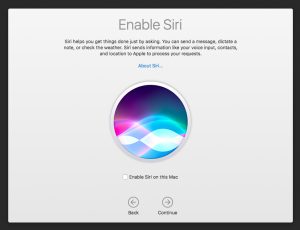
Do you really want to talk to your Mac?
In late September, Apple introduced Mac OS X.12, (Sierra) as a free upgrade, available (as usual) in the App Store. While there are some features that will have Apple fanboys and fangirls excited (Siri on the Mac, the ability to login to your computer via your Apple Watch), most of the action takes place behind the scenes. In other words, functional, but not all that exciting.
There have been a few small glitches with OS X.12. One is an incompatibility issue with Microsoft Office 2008. If you’re planning to upgrade to Sierra, then it’s time to move on from Office 2008, a software package that’s approaching its ninth birthday. Another is a strange pixilation of the print window in some programs (Adobe Acrobat, for example), but that appears to be only an aesthetic issue, not a functional one. And I’m reading of nightmares when mixing Sierra and QuickBooks, so if you’re a QB user, don’t even think of upgrading until you receive the “all clear.”
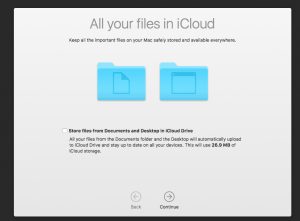
Think before blindly syncing your files to the cloud!
But the biggest issue I have discovered with updating to Sierra is during the configuration process, post restart, after the software has been downloaded and installed. There is an option to enable Siri (see graphic above), but the next one that comes along – to move all your documents into iCloud Drive – is troubling. That’s because you potentially will be forced into upgrading (e.g. paying Apple for more storage capacity). Worse, your data will have been forcibly migrated into “your” iCloud Drive (which means it’s also stored on Apple’s servers somewhere out there).
iCloud Drive’s tagline is “All your files. On all your devices.” Which is fine and dandy – but that’s exactly what Google Drive, Dropbox and others do just as well. Doing something as rash as moving all your files out of their familiar homes and into the cloud is something you need to put a lot of thought into – not just go willy-nilly with the defaults of an OS update and hope for the best. Understanding exactly how iCloud Drive works and exactly why you would want to take such a large step with your valuable data are things best thought out beforehand.
It’s like deciding who to vote for after the curtain closes behind you in the voting booth. Not the best way to handle an important decision.
June 16, 2014

Last month, while working at a client site, I was checking my email while waiting for something to install on the client’s Mac. I casually deleted a couple of unread messages – Groupon and Macy*s – without reading, and was asked “how can you delete an email without reading it?”
There’s an easy answer; the Groupon wasn’t interesting to me, plus I can easily go to its site to see ALL of the offers, and I wasn’t planning on shopping at Macy*s this week. So BOOM – off they go into my Deleted Items. I’ve seen too many people with 10,000+ UNREAD messages in their inboxes – bad news! Not only does a loaded email box make things run more slowly, it takes up valuable hard drive space and can cause the mail program to bonk, sometimes resulting in the loss of many of those messages.
All through my years of working in the industry, whether it’s in a corporate IT environment, a tech writing job or just freelance, I’ve gotten pretty slick at keeping my inbox empty, or at least at a manageable level. I’ve come up with a few easy-to-implement tricks to keep things from spiraling out of control. Yes, it does take some work on your part – but spending a couple of minutes a day keeping things tidy is preferable to paying a professional big bucks to reconstruct your email.
In no particular order, here is a six-pack of tips to avoid being a digital hoarder:
#1) Establish a second email address for retail subscriptions, as well as other mailing lists.
Adding a second (or third) email account to handle mailing lists is a stellar idea, particularly now that we’re all using iPads and iPods to get our mail. This serves two purposes – it keeps our “real” inboxes free of non-essential messages, and because most of these mails are timely, it’s easy to delete them in bulk. I can’t begin to tell you how many users still hold onto J. Crew messages announcing a sale that expires in October 2011.
#2) Unsubscribe from all mailing lists and newsletters that aren’t important to you. (Except mine!)
Just be honest – if you don’t read an email soon after you receive it, it’s probably irrelevant anyway. And question if it’s even pertinent to your situation – if you’re on the Hilton Properties list because you stayed at one of its hotels recently, does any news from them have any bearing on what you’re doing now?
#3) Configure your email client to “Quote The Text Of The Original Message”
Having all of the previous email messages referenced in the current correspondence is another way to keep your inbox pared down. That way you need to save only the most recent message to have access to the entire string. In 99.9% of situations this is fine; however, in cases that require lawyers, documentation and court dates, you should save EVERY message! (In a dedicated folder, as described below.)
#4) Create separate folders for completed tasks.
If you need to save archive old email messages, store them in newly created folders to help clear out your inbox. Not only does this help keep your inbox neat and clean, it also helps your overall organization. Create as many of these folders as you need; you can organize them by sender, project or date.
#5) Create a “Pending Issues” subfolder to store messages that require action on your part.
The “Pending Issues” folder isn’t simply a storage bin to bulk offload messages from your inbox – think of it as a “to do” list for your action items.
#6) Be at peace with the fact that you’re NEVER going to read those old emails.
Human nature is funny – there are some things in life that everybody believes they possess; personal style, a sense of humor, good driving skills and excellent taste in music. Add one more – the belief that they’re someday going to read those old emails. It’s not going to happen. And the sooner they come to that realization, the better off mankind will be.
May 15, 2014
It seems that we’re constantly being hammered with updates. And not just from Apple, but from Adobe, Mozilla and Microsoft, among others. Many others. I get a lot of calls from clients, citing concern about applying updates. In most cases, notifications for updates on the Mac platform are legitimate, but there are instances where scammers send out official-looking email notices that request that you update your software.
One thing is certain; you will want to verify that the update request is bona fide and not a scam. The best way to stay protected from a scam that is to instigate all updates yourself. So don’t count on an email to be legit – learn how to perform updates on your own and learn to ignore the fake requests, similar to the way you dismiss the bogus FedEx delivery notifications and Nigerian money transfer scams.
The bottom line: NEVER rely on an email notification (or phone call) to inform you of an update. In addition, performing an update indicated by a pop-up window on a Website is also a bad idea, but you have to be able to differentiate between a Web pop-up and a legitimate notification from Apple. What you SHOULD do is be proactive and take a few minutes from time to time to initiate all the updates on your computer yourself.
To see a list of the most common updates you should perform, visit my update resource page here.
April 16, 2014

This month, the Heartbleed bug is all over the news. In short, it’s a security flaw that leaves a large percentage of the world’s Internet servers susceptible to hackers. While in theory it doesn’t pose any risks with the data on your personal computer, it still is a major concern because it potentially leaves a large number of user names and passwords exposed to the bad guys.
While these user names and passwords might be on sites where a stolen identity may be on the “no harm no foul” side of the ledger (www.sobe.com, for example), these same user name/password combinations MAY be the same on sites (such as online banking) where you certainly don’t want any unauthorized access.
While companies out there in cyberspace are scrambling to get these security holes patched up, you can help yourself by changing your passwords to most (if not all) of the sites you visit. That can be a tedious process, and although there are apps that can help automate things, it’s best to do it only AFTER you’ve checked if the site has been upgraded to eliminate the security breach. A good resource to check if a site has been repaired its Qualys SSL Labs.
Another great resource for is an e-book titled “12 Quick Tips for Creating, Recording & Remembering Your Computer Names & Passwords” written by yours truly. It’s available from Amazon. You can read it on the iPad if you have the Kindle App installed. It’s also available from Apple’s iBooks Store. If you don’t already have it, you can download the iBooks app from Apple’s App Store for free.
March 11, 2014
![]()
Just when everything seems to be working well, you get the dreaded SMTP error and your outgoing email remains stuck in the Outbox. Yet you’re able to seamlessly receive email messages. So what’s the deal with that?
That’s because, for some reason (and Apple will never admit there is a problem with its software), its Mail program has trouble with outgoing mail. Yes, even though it worked fine an hour ago and you haven’t tinkered with the settings, you’ll still get an error message when attempting to send email. The message usually reads “Cannot send message using the service mail.optonline.net” or something similar.
Does this happen to you? And do you know what to do when you get this message? It seems it’s a flaw in Apple’s Mail program. Users with Optimum as their ISP (Internet Service Provider) tend to have this issue, but it’s not limited to Cablevision users; other email providers fall prey to this glitch.
I’ve found that the best way to quickly fix this issue is to delete the outgoing mail server and then reinstate it. This is accomplished by performing the following:
If you’re using an outgoing (SMTP) server that isn’t Optonline, then you should consider making print screen of the information (Command-Shift-4) for your records. And please record your password! If you need help with your passwords, I suggest an extremely helpful e-book, 12 Quick Tips for Creating, Recording & Remembering Your Computer Names & Passwords, available at Amazon as well as Apple’s iBooks Store.